How do macOS users quickly access the lock screen? A crucial component of security and efficiency, this feature offers streamlined access to critical functions.
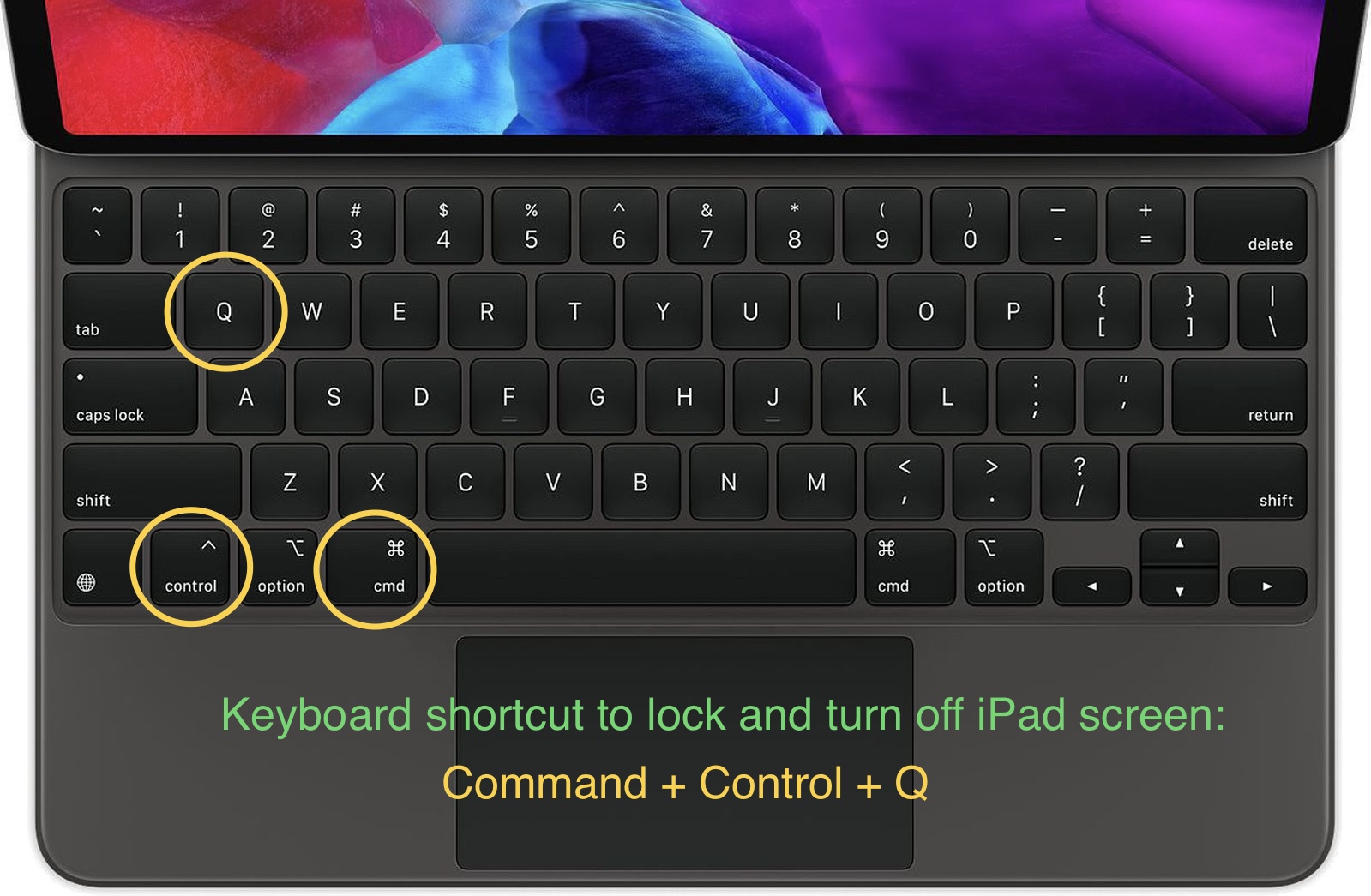
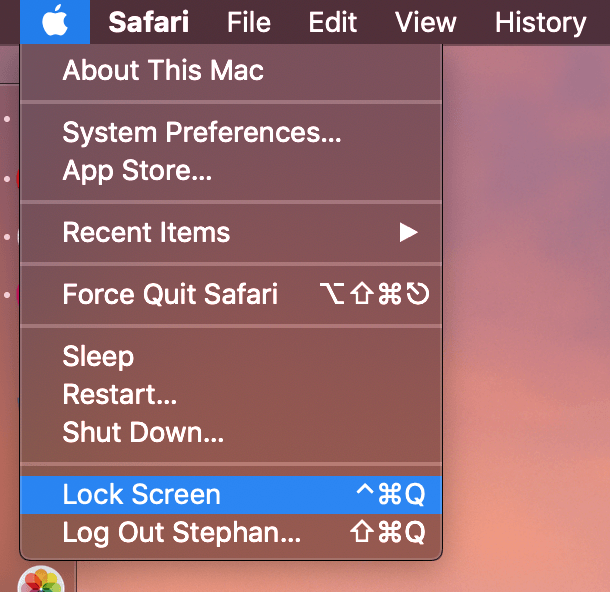
A shortcut for accessing the lock screen on macOS enables immediate control over screen security and user authentication. This often involves a specific keyboard combination, mouse click, or menu item, bypassing the typical full-screen login. For example, pressing Command + Control + Q may initiate the lock screen, varying according to the macOS version. This shortcut can be vital for quickly securing a Mac when temporarily unattended, facilitating secure user transitions, or enforcing a defined access level, especially for shared computers.
Rapid lock screen access significantly enhances security. This swiftness minimizes the opportunity for unauthorized access, important in both personal and professional contexts. Furthermore, the ability to immediately lock a system can prevent unintended data modification or sensitive information disclosure. The functionality also plays a key role in the overall security architecture of macOS, mirroring other operating system features that prioritize user accounts and data protection.
This discussion now transitions to the detailed exploration of specific macOS keyboard shortcuts, different lock screen configuration options, and practical examples of how these shortcuts can be utilized in various scenarios.
Mac Lock Screen Shortcut
Efficient access to the Mac lock screen is crucial for maintaining system security and user control. Understanding its key elements is essential for optimized operation.
- Security
- Convenience
- Accessibility
- Keyboard
- Authentication
- Configuration
- Functionality
These aspects are interconnected. Security is paramount, achieved through swift access. Convenience is enhanced via keyboard shortcuts, optimizing workflow and minimizing the time spent unlocking. Accessibility ensures the shortcut is usable for all user levels. Keyboard shortcuts represent the fundamental interface for this function. Authentication, whether password or biometric, is vital with rapid lock screen access. Configuration enables customization, and functionality includes the broader scope of secure login management. For example, a robust security system necessitates the efficient functionality of keyboard shortcuts for quick locking.
1. Security
The relationship between security and a Mac lock screen shortcut is fundamental. A swift and easily accessible lock screen shortcut is a direct component of a robust security posture. A compromised system, where unauthorized access is possible, is demonstrably less secure. Prompt locking, achieved through a shortcut, serves as a crucial preventative measure against potential threats. This rapid response to a potential security lapse is critical in mitigating the impact of a breach. Examples include situations where a user briefly steps away from their workstation, or when multiple users share a system, requiring rapid access to account security.
Practical applications of this understanding are substantial. Organizations handling sensitive data rely heavily on this functionality, enabling instant safeguarding against unauthorized access. For individual users concerned about personal privacy, it's essential to appreciate the role of a quick lock screen shortcut as a deterrent to data breaches. The ability to lock the system immediately minimizes the time a device is vulnerable, thereby significantly lowering the risk of unwanted or malicious actions. The seamless integration of secure user authentication into the workflow, via the shortcut, reinforces the overall system security, making it a key element in protecting confidential information and digital assets.
In summary, the direct connection between a secure lock screen shortcut and overall system security is undeniable. A swift response to potential threats, achievable through a well-designed shortcut, is a critical element of a secure computing environment. This understanding emphasizes the importance of well-placed security measures to protect against threats and ensures the privacy of individual and organizational data. This highlights the practicality of incorporating lock screen shortcuts into any strategy aimed at robust security measures within a macOS environment.
2. Convenience
A streamlined lock screen shortcut contributes significantly to user experience. Efficiency in accessing security features directly impacts productivity and usability. This aspect is crucial for optimizing workflow and preventing disruptions.
- Reduced Time to Secure
A well-designed lock screen shortcut minimizes the time required to secure a Mac. This streamlined process is particularly valuable when users need to quickly step away from their computers. The immediacy of the shortcut eliminates unnecessary steps, allowing users to focus on their tasks without delays or disruptions. For instance, a quick shortcut allows a user to leave a meeting, knowing the system is immediately protected against unauthorized access.
- Improved Workflow Continuity
A readily accessible lock screen shortcut maintains workflow continuity. The user can resume work without interruption when returning to the device, preventing lost progress or requiring re-authentication. This predictability and streamlined process contribute to a more efficient work environment. For example, a user can temporarily step away from a presentation, lock the computer, and return without having to re-enter passwords or configurations.
- Enhanced User Experience
A user-friendly shortcut enhances the overall user experience. Simple and intuitive shortcuts enable users of all skill levels to easily access the lock screen. This direct access minimizes frustrations and simplifies interacting with the operating system, especially for frequent transitions between active and secured states. The smooth and efficient operation of the lock screen shortcut contributes to a positive and efficient user experience.
- Seamless Transitions Between Users
For shared computers, a readily available lock screen shortcut facilitates seamless transitions between users. This expedites the hand-off process, preventing unnecessary delays. Quick lock and unlock enables a quicker handover between users and streamlines the transition process. Examples include a team environment where individuals frequently share work computers. Rapid and efficient lock and unlock simplifies the workflow.
In conclusion, a well-executed lock screen shortcut directly improves convenience. This enhancement is reflected in reduced time spent securing the computer, improved workflow efficiency, a positive user experience, and smoother transitions for shared devices. The immediate access to security features is fundamental in promoting a productive and uninterrupted work environment.
3. Accessibility
Accessibility considerations are paramount when designing a lock screen shortcut for macOS. A user-friendly approach ensures equitable access to crucial security features for individuals with varying abilities. This aspect necessitates a thoughtful design for diverse users, acknowledging potential needs and limitations.
- Keyboard-Only Navigation
A lock screen shortcut should function seamlessly with a keyboard alone. This consideration is critical for users who may not be able to use a mouse or trackpad effectively. Providing clear, logically ordered keystrokes for various actionssuch as locking, unlocking, or navigating menu optionsis essential. This approach accommodates users with disabilities and those working in environments where a mouse might not be readily available.
- Visual Clarity and Contrasts
Sufficient visual contrast and clear formatting of lock screen elements are vital. A user with visual impairments needs the ability to perceive visual cues and interface elements easily. This includes proper font sizes, appropriate colors with sufficient differences, and easily readable prompts or instructions. Such considerations ensure usability by all users.
- Proper Prompting and Feedback
The system should provide appropriate feedback after a shortcut is executed. This feedback should clearly indicate whether the lock screen has successfully activated or if there are issues. This might include audible signals or distinct visual cues, ensuring confirmation of action and enabling the user to understand the operation's status promptly. This is particularly critical for users with auditory or visual processing differences.
- Customization Options
Offering configurable options for the shortcut's functionality allows users to tailor the experience to their needs and abilities. For instance, enabling or disabling visual effects or modifying feedback mechanisms can be beneficial in a personalized approach to the user experience. Such customizations account for varying preferences and needs among users.
These aspects of accessibility are not merely beneficial additions but rather crucial components in ensuring usability. A well-designed lock screen shortcut that adheres to accessibility principles is vital for a positive user experience across diverse user groups. Failing to prioritize accessibility compromises the overall usability and efficiency of the feature for a wide segment of potential users.
4. Keyboard
The keyboard serves as the primary interface for initiating macOS lock screen shortcuts. Its role in enabling rapid access to security features is critical for efficient system management. Understanding keyboard shortcuts directly impacts user experience and operational security. Swift and intuitive access to locking mechanisms is central to the overall design and functionality of the macOS system.
- Keystroke Combinations
Specific key combinations, such as Command+Control+Q, often activate lock screen functionality. These combinations are frequently customizable, allowing users to tailor the shortcut to personal preferences. The design of these shortcuts is crucial in ensuring usability, minimizing errors, and promoting a streamlined interaction process. Different macOS versions might require or implement different key combinations.
- Direct Control over Security
Keyboard shortcuts provide direct control over screen security. This immediate access allows swift response to various situations, from temporary unattended use to user transitions, improving system protection. The reliance on keyboard shortcuts highlights the direct interaction between user input and system security protocols.
- Accessibility and Inclusivity
Keyboard shortcuts are crucial for accessibility. Users reliant on keyboard input are not excluded from system security functions. This design consideration ensures the practicality and inclusivity of the operating system for individuals with different abilities. The accessibility of keyboard shortcuts underscores the importance of accommodating diverse user needs in the design of macOS.
- Historical Context and Evolution
The implementation of keyboard shortcuts for lock screens has evolved across macOS versions. Early iterations might have used different keystroke combinations, reflecting the continuous development and improvement of the OS. This evolution of key combinations demonstrates the ongoing integration of security and user experience features within the operating system.
Keyboard shortcuts are fundamental to accessing the lock screen swiftly and securely on macOS. Their design emphasizes security, user experience, and accessibility. The consistent use of keystroke combinations across various macOS versions promotes familiarity and efficiency for users.
5. Authentication
Authentication is integral to the security afforded by a Mac lock screen shortcut. The method of confirming a user's identity directly influences the effectiveness of the security mechanism. A robust authentication process, seamlessly integrated with the shortcut, is essential for preventing unauthorized access to the system.
- Password-Based Authentication
Password-based authentication, a common method, relies on a unique password associated with a user account. The lock screen shortcut, in this case, initiates a prompt for the password, requiring the user to input the correct credentials. Examples include personal computers, corporate networks, and shared devices. Failure to enter the correct password prevents access to the system, directly linked to the shortcut's purpose of securing the Mac.
- Biometric Authentication
Biometric methods, such as Touch ID or Face ID, utilize unique physiological characteristics to authenticate users. The lock screen shortcut integrates with these methods, allowing authentication through fingerprint or facial recognition. This approach, often considered more secure than password-based methods, directly impacts the shortcut's function in facilitating swift, secure logins. For example, in personal devices, biometrics are used for quick unlocking, reflecting the streamlined nature of the shortcut.
- Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security. The lock screen shortcut can initiate the second verification step, often a code sent to a registered mobile device. This two-step process significantly enhances the security of the system when combined with a lock screen shortcut. Examples include financial transactions and highly sensitive data access; such use cases underscore the importance of robust authentication in conjunction with lock screen shortcuts.
- Security Considerations and the Shortcut
The chosen authentication method significantly impacts the overall security of the system and is inextricably linked to the effectiveness of the lock screen shortcut. Weak authentication processes diminish the strength of the security measures, rendering the shortcut less effective in protecting the system. Conversely, robust authentication paired with a well-designed shortcut creates a highly secure environment.
In summary, the type of authentication implemented directly affects the efficiency and security provided by a Mac lock screen shortcut. Choosing appropriate and robust authentication methods is crucial. This ensures the effectiveness of the shortcut in preventing unauthorized access and securing the system. The seamless integration of authentication mechanisms with the shortcut is critical for optimal security and user experience.
6. Configuration
Configuration plays a pivotal role in the functionality and effectiveness of a Mac lock screen shortcut. Appropriate configuration settings are essential for customizing the shortcut to meet specific security needs and user preferences. Without proper configuration, the shortcut might lack crucial features or not align with the desired security level. This intricate connection is vital for ensuring the intended purpose of the shortcut is achieved, whether for individual or organizational use.
The configuration of a lock screen shortcut involves several key elements. Customization options often include the ability to select or disable specific authentication methodspassword entry, biometric verification, or two-factor authentication. These choices directly influence the complexity and security level of the lock screen prompt. Further configuration might involve setting time-outs for inactivity, specifying keyboard combinations for activation, and altering visual aspects of the lock screen itself. Each setting impacts the shortcut's overall efficiency and responsiveness. For example, configuring an extended inactivity timeout might be beneficial in a collaborative workspace, while a shorter timeout is more appropriate for individual use. Different configurations cater to diverse user needs, from personal devices to corporate environments.
Understanding the configuration options available for a lock screen shortcut is critical for maximizing its security and efficiency. Proper configuration ensures the shortcut's alignment with the user's needs and security priorities. By understanding and utilizing the various configuration options, users can tailor the lock screen shortcut to their specific requirements, whether enhanced security measures for sensitive data, simplified access for individual use, or optimal performance for shared devices. An understanding of how configuration impacts the shortcut's operation is essential for effective implementation and security optimization. This direct relationship highlights the importance of carefully examining and adjusting configuration parameters to maintain a balance between security and usability.
7. Functionality
Functionality, in the context of a Mac lock screen shortcut, encompasses the practical actions and operational capabilities of the feature. This aspect encompasses how the shortcut interacts with the system, ensuring seamless security and user experience. Understanding these operational characteristics is vital for evaluating the effectiveness and utility of the feature.
- Initiation and Activation
The functionality begins with the triggerthe designated keystroke combination or action. Activation is the system's response to this input, initiating the lock screen process. A functional shortcut enables rapid transition to a secure state. Examples include the lock screen appearing instantly after the user presses a designated key combination. This responsiveness and direct activation are crucial elements of the shortcut's utility.
- Authentication Integration
Functionality extends to the seamless integration with authentication protocols. The system's response after the initiation of the shortcut triggers the required user authentication process. A secure lock screen requires effortless navigation through password entry, biometric verification, or other security measures. A malfunction in this authentication aspect directly undermines the shortcut's effectiveness. For example, a user initiates the lock screen, and the subsequent authentication process is not correctly initiated. This jeopardizes the system's security.
- User Experience and Feedback
Effective functionality encompasses user experience. The system must provide clear feedback on the status of the lock process. This feedback may include visual cues, auditory signals, or both. Clear, immediate feedback reinforces user understanding and confirms the lock screen's successful activation. The lack of clear feedback can lead to confusion and frustration.
- System Lock and Security Implementation
Functionality extends to the system's actions immediately following lock-screen activation. The system must enforce a secured state, preventing further access until the appropriate authentication procedures are completed. This direct system response to the shortcut is critical for data protection. A failing system lock implementation, in response to the lock screen activation, reduces the integrity and security provided by the shortcut. A successful implementation ensures that any system activity is blocked once the lock screen is initiated.
The functionality of a Mac lock screen shortcut hinges on its efficiency, security, and user-friendliness. These interconnected aspects collectively define a positive user experience, a robust security posture, and a dependable locking mechanism. The correct implementation of each facet is essential for a successful and comprehensive lock screen shortcut. Failure in one area directly impacts the overall functionality, thereby impacting the entire system security framework.
Frequently Asked Questions
This section addresses common questions regarding Mac lock screen shortcuts, providing clear and concise answers to ensure a comprehensive understanding of this essential macOS feature. Accurate information about the functionality and use of these shortcuts is crucial for efficient and secure system operation.
Question 1: What are the typical keyboard shortcuts for accessing the Mac lock screen?
Different macOS versions might employ various keyboard combinations. Consult the macOS documentation for the specific version being used to ascertain the exact sequence. Common methods involve combinations of Command, Control, and other keys. General guidance should be found within the operating system's help files.
Question 2: How do I customize lock screen shortcut options?
macOS settings generally offer a range of customization options. These vary based on the specific operating system version. Consult the System Preferences within the macOS settings menu to determine available options for keyboard shortcuts and related configurations. Specifics may be found in online guides or tutorials.
Question 3: Are there accessibility considerations for lock screen shortcuts?
Yes, accessibility is important. Options might exist for adjusting keyboard shortcuts to be compatible with assistive technologies. Consulting the macOS accessibility features section can provide details on making the shortcut more suitable for individuals with specific needs. This ensures a broad range of users can effectively leverage the lock screen shortcut.
Question 4: How does authentication integration affect lock screen shortcut effectiveness?
The choice of authentication methodpassword, biometric, or two-factorsignificantly impacts the shortcut's security. Stronger authentication methods result in more robust security, directly enhancing the shortcut's effectiveness. A system requiring stronger authentication will often have more robust configuration options available.
Question 5: What are the implications of using a lock screen shortcut in a shared environment?
In a shared environment, the frequency of use and prompt security mechanisms become crucial. Proper configuration and consistent authentication routines are necessary to safeguard data. Consider the necessity for quick-lock features for seamless user transitions and the potential sensitivity of data being accessed.
Understanding these factors ensures users effectively utilize the lock screen shortcut while maintaining a secure and controlled environment.
This concludes the frequently asked questions regarding Mac lock screen shortcuts. The next section will delve into practical examples and scenarios of employing these shortcuts within various user contexts.
Conclusion
The exploration of Mac lock screen shortcuts reveals a multifaceted feature critical to system security and user experience. Key aspects, including security, convenience, accessibility, keyboard integration, authentication methods, configuration, and functionality, all contribute to the overall effectiveness of this feature. The swiftness of lock screen access is directly tied to the system's protection against unauthorized access, crucial in a variety of contexts, from personal use to enterprise settings. The operational characteristics of the shortcut, from initiation to authentication, impact user experience and overall system security, reinforcing its importance in maintaining data integrity and privacy. Customizable configurations allow users to tailor the shortcut to their specific needs and security priorities, providing flexibility for diverse environments and user preferences.
In conclusion, a well-implemented Mac lock screen shortcut is an essential component of a secure and efficient computing environment. Effective integration of security protocols, efficient operational design, and accessibility considerations all contribute to its utility. Understanding the diverse applications and implications of these shortcuts is vital for maintaining a robust security posture and optimizing the user experience. Ongoing improvements and adaptations to the feature in future macOS versions will undoubtedly ensure its continued relevance and effectiveness in the evolving technological landscape.
Article Recommendations